Configure AD FS
Prerequisites
To set up Active Directory Federation Services (AD FS) SSO in DronaHQ, you will need:
- Access permissions to create a relying party trust in your ADFS settings.
- Manage Users access on self-hosted DronaHQ instance or DronaHQ Cloud to configure SSO configurations.
Creating a Relying party Trust in ADFS
Follow the Relying Party Trust wizard in Active Directory with the following settings.
- In
Select Data Source, selectEnter data about the relying party manually. - In
Choose Profile, selectAD FS profile. - In
Configure Certificate, do not upload a certificate. - In
Configure URL, selectEnable support for SAML 2.0 WebSSO Protocol. Download and Open DronaHQ metadata file. To locate this file, Go toDronaHQ -> Manage Users -> SSO CONFIGURATION -> + Add SSO -> SAML 2.0, Under Entity ID and Metadata URL open this url file. Configure URL is the location where SAML assertion is sent with anHTTP POST, known asSAML Assertion Consumer Service URL. Locate this in the Metadata downloaded and paste it here. Ex - https://studio.dronahq.com/callback/saml. - In
Configure Identifiers, add your single-sign on domain without the protocol as aRelying party trust identifier. For example, usedronahq.yourcompany.cominstead ofhttps://dronahq.yourcompany.com. Finish the wizard.
Create rule to Send LDAP attributes as claims
Follow the steps to send LDAP attributes as claims.
- On the
Choose rule typepage, selectSend LDAP Attributes as Claims. - On the
Configure claim rulepage, chooseActive Directoryas the attribute store. Fill in the following settings.
| LDAP Attribute | Outgoing Claim Type |
|---|---|
| Email addresses | |
| Email addresses | AD FS 1.x Email address |
| Given Name | name |
- Select
Transform an Incoming Claimand select the following settings.
| Setting | Value |
|---|---|
| Incoming claim type | AD FS 1.x Email Address |
| Outgoing claim type | Name ID |
| Outgoing claim ID format |
- Select Pass through all claim values and save the settings.
Configure in DronaHQ
In order to configure SAML in DronaHQ, we will need metadata file from your IDP. There is usually a button to download this from your IdP dashboard. Additionally, you can often find this by navigating to https://your.identityprovider.com/federationmetadata/2007-06/federationmetadata.xml.
- Now that we have metadata file, In DronaHQ, Go to
Manage Users -> SSO Configuration -> + ADD SSO -> SAML 2.0
Enter form with below fields -
| Field | Description |
|---|---|
| Name | Provide Friendly Name of this SSO configuration |
| Entity ID | The entity ID is present in metadata file. Copy the ID and paste it. |
| Login URL / SSO URL | Enter the details of location of singlesignonservice from metadata file for POST method. |
| X509 public certificate | X509Certificate file in .cer format. This file you can create following this step whose content you can locate in the metadata file. |
| Binding type | Enter HTTP POST. |
| Restricted Domain | Enter domain name for which you want your users to login with for this SSO Configuration. You can add multiple domain names as well. eg - domain1.com , domain2.com. DronaHQ will automatically redirect to SSO url when we encounter any user’s sign in request with an email id belonging to the given restricted domain. |
| Want Auth request signed | Locate this your IDP metadata file. Usually, Keep this default setting as False. |
| Add Claim List | We have already assigned Email and Name in ADFS. We will now enter same key name - email and name and map it to DHQ User Name and DHQ User Email respectively. |
| Enable JIT user provisioning | Toggle this ON so that you won’t have to manually invite each user to DronaHQ first. |
| Enable SCIM User Provisioning | Enable this in case you want to create, update and deactivate User accounts at your IDP portal and sync it with DronaHQ user management. |
- Save the draft. Again navigate back to the SSO configuration option. You can see the newly created SAML.
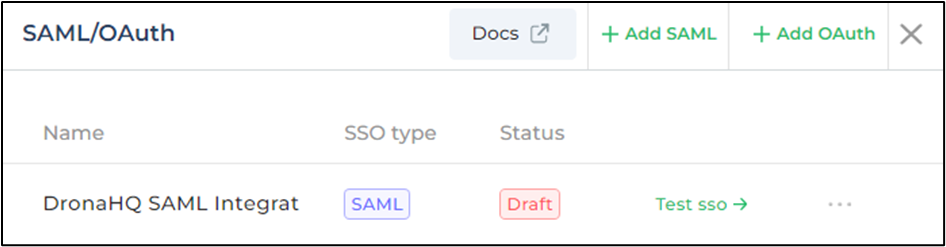
You can click on
Test SSObutton and it will open SSO Login url in a popup window.Once you login successfully and if everything is set up correctly, then finally you will see a success message at the bottom.
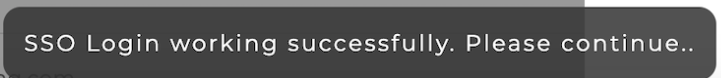
- Now, that testing is successful, you can click on the more option for above SSO configuration and click on
Activateto make it live.

ADFS SAML in Action
Now, since our ADFS SAML SSO is live, we check in either DronaHQ End user portal - Web, Android or iOS and see our configured adfs saml sso in action.
Simply go to DronaHQ End user webapp and enter your email id with domain that matches the configured restricted domain specified in SSO configuration and Click Continue.

Instead of asking for password, it asks for Login via SAML SSO provider. Click on it and open a popup window of your idp and the user can login with your idp login credentials.
Go to Manage User section on DronaHQ and you will see the new user created since JIT was enabled.